In last few posts, we have understood the concept of RODC. This will be the last post in RODC series where we will know the necessary settings for newly installed RODC. As we saw in last post, that only installing RODC is not sufficient as it has to reach to the writable DC every time any user wants to login through RODC. To enable the RODC to handle the authentication itself, we have to understand two concepts:
- Password Replication Group: This is the special group for RODC to make them capable to replicate passwords of all users.
- Credential Caching: It will allow RODC to save the credentials locally to let users authenticate quickly.
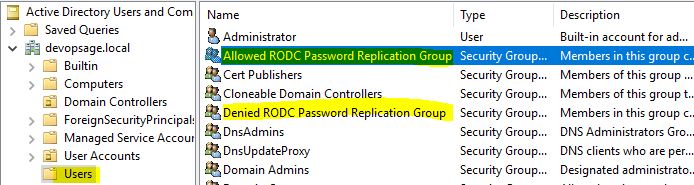
Open “Active Directory Users and Computers” and go to “Users” container. There you will find two special groups for RODC:
- Allowed RODC Password Replication Group: Members of this group can replicate account passwords across the domain.
- Denied RODC Password Replication Group: Members of this group can’t do anything in terms of password replication. In case a user is part of both group, Deny group will take the precedence.
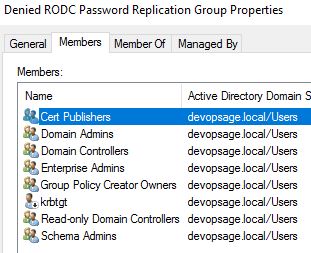
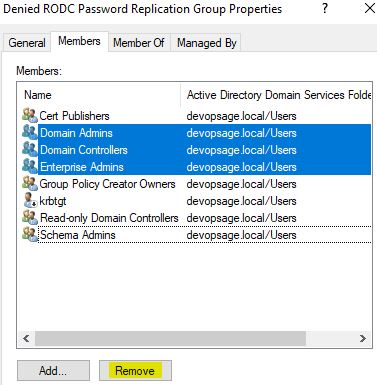
By default following accounts will be part of Denied RODC Password Replication Group. You can, and you have to customise this membership.
Login to any Writable DC, open “dsa.msc” and navigate to “Domain Controllers” OU. There you will find the list of all DCs, including RODC. Right click on the RODC you want to enable for password replication and go to Properties.
- Note: You have to do it in writable DC only as in RODC you can’t do any changes.
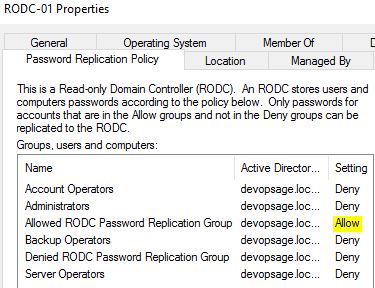
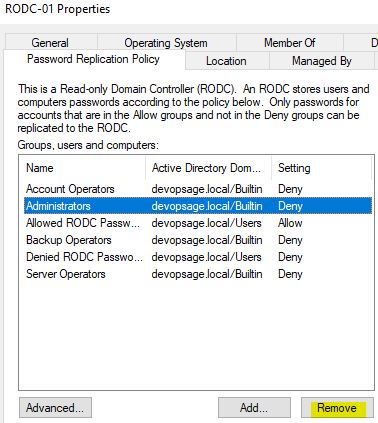
There you will find a special Tab called “Password Replication Policy”, which you can’t find in normal DC. There you can see all the accounts and groups who are allowed or denied for Password Replication. By default Allowed RODC Password Replication Group and Denied RODC Password Replication Group will be there and set for Allowed and Denied respectively.
From there, I am removing Administrators, as I need them to be capable to replicate password.
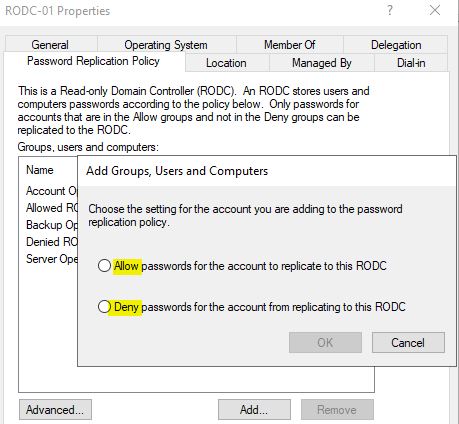
Similarly from there, you can try to add any user or group for allow or deny replication. However I strongly recommend to simply add the users or groups to Allowed RODC Password Replication Group to avoid any complications.
To do that, I will go to Denied RODC Password Replication Group and remove all accounts which I want to be able to replicate the password.
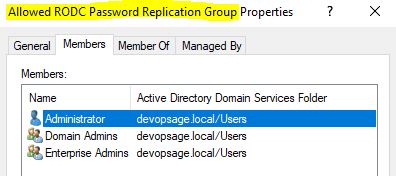
Now I will go to Allowed RODC Password Replication Group and add all accounts which I want.
Once done, login to RODC and run “gpupdate /force” command to refresh the policies. After that you will be able to login to RODC even if writable DC is down.
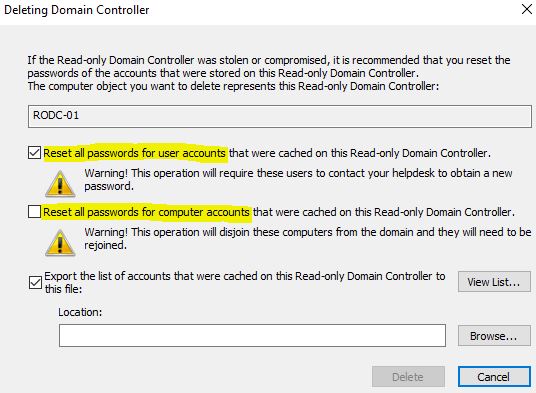
Your RODC is now enable to replicate password and credential caching. If you try to delete your RODC, it will ask you to also reset all the cached credentials.
Hope this article will help you. Cheers!